Access Control
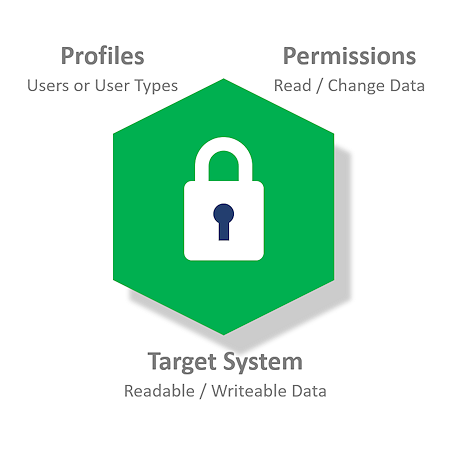
We simplify access control by reducing implementation to an easy and rapid process of association.
Designers configure our wireless devices to manage access to specific variables in their target system's memory. To do this they simply "bundle":
- Resources (variables/registers in target-system memory)
- Profiles (standard or customized user types)
- and Permissions (read and/or write access rights)
Access control configuration is simple to implement and then evolve over time. Implementing and adapting thes access control mechanisms doesn't require you to write a single line of code.
Find a Secure Wireless Product...
Instantly add secure wireless to any electronic design. Create custom UI apps in a few clicks, or integrate with any cloud platform with just a few lines of java.

Transform serial fieldbus or Modbus® ports into secure wireless for mobile servicing apps. Create a custom UI directly on your mobile, or create your own servicing app in a few clicks.

Retrofit serial fieldbus or Modbus® ports with secure wireless for the IIoT. Create custom UI directly on your mobile, or create your own servicing app in a few clicks. Integrate with any cloud platform with just a few lines of java code.



